Table of Contents
- 1. Problem Statement
- 2. Target Vision
- 3. Solution Approach
- 4. Implementation in Kubernetes
- 5. Special Features
- 6. Pod Manifest
- 7. Conclusion
- 8. Frequently Asked Questions
Meet the Author
2025-05-06
Build a secure IPsec-VPN tunnel out of KubernetesStrongSwan VPN in Kubernetes: Securely Integrate External Services
In some cases, a VPN connection to an external service is needed - which can be tricky with Kubernetes. In this article, we show how to set up an IPsec tunnel with StrongSwan. From Kubernetes to an external service using Nginx as a reverse proxy. The setup is clearly structured, easily maintainable, and dynamically distinguishes between staging and production environments.
Prerequisites
You should have the following knowledge to use the article optimally:If you have any questions or if anything is unclear, you can use the comment function below the article.
1. Problem Statement
Sometimes an important database is not in the cluster itself, but behind a firewall on an external server. Access is only possible via a VPN - for example via IPsec with a WatchGuard Appliance. The challenge: How can applications in the cluster reliably and securely reach this service?
2. Target Vision
The goal was to create a lean and maintainable solution that:
- Can access fixed defined external services via VPN from within the cluster,
- Clearly distinguishes between Staging and Production access,
- Remains flexibly configurable,
- Works with Kubernetes standards (Probes, Services, ConfigMaps etc.).
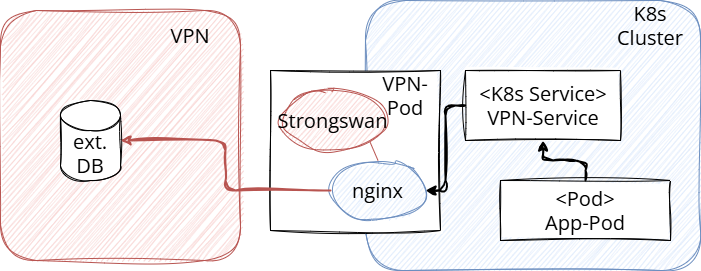
3. Solution Approach
We deployed a dedicated pod with Strongswan and Nginx:
- Strongswan handles building the IPsec tunnel to the external VPN endpoint.
- Nginx functions as a TCP proxy and forwards requests from the cluster to the external service.
- Depending on the environment (Staging or Production), Nginx is configured accordingly.
Within the cluster, other services can easily access Nginx via ClusterIP, which then transfers the connection over the VPN.
4. Implementation in Kubernetes
a) Dockerfile
Nginx and Strongswan run side by side in the container. A startup script decides which configuration files to use based on the ENVIRONMENT variable.
FROM nginx:1.27.3-alpine
RUN apk add --no-cache strongswan netcat-openbsd
...
CMD ["/scripts/startup.sh"]
b) Nginx Configuration
For Production, there's a single TCP forwarding (e.g., on port 8080), while the staging environments has two (8080 + 8081 for production/staging).
stream {
upstream ext-db-production {
server NGINX_EXTDB_IP_PRODUCTION:NGINX_EXTDB_PORT_PRODUCTION;
}
server {
listen 8080;
proxy_pass ext-db-production;
}
...
}
We can also connect your Kubernetes apps via VPN.
b) VPN-Setup with Strongswan
The tunnel is configured dynamically via swanctl.conf and environment variables. This allows IP addresses, PSK and subnets to be imported via a Helm template.
connections {
k8s-ext-db {
remote_addrs = SWANCTL_CONF_REMOTE_ADDRS
local {
auth = psk
id = SWANCTL_CONF_LOCAL_ID
}
remote {
auth = psk
}
children {
net-net {
local_ts = SWANCTL_CONF_LOCAL_TS
remote_ts = SWANCTL_CONF_REMOTE_TS
esp_proposals = SWANCTL_CONF_ESP_PROPOSALS
...
}
}
version = 2
proposals = SWANCTL_CONF_PROPOSALS
...
}
}
secrets {
ike-k8s-nors {
id-k8s = SWANCTL_CONF_LOCAL_ID
secret = SWANCTL_CONF_SECRET_PSK_TOKEN
}
}
The capitalised variables in all config files are replaced by the startup script with values from the environment variables. This allows the pod to be configured dynamically for different environments. The values could of course also be specified directly.
The startup script then only performs the following commands to establish the VPN connection:
swanctl --load-all
ipsec up k8s-ext-db
d) Health Probes
A shell script checks regularly:
- the VPN target IP is reachable:
nc -z -w 1 $PROBE_STRONGSWAN_IP $PROBE_STRONGSWAN_PORT - the internal Nginx serves a
/healthzroute:curl -f -LI $PROBE_NGINX_IP:$PROBE_NGINX_PORT/healthz
The exit code will only return 0 if both conditions are met. This makes it easy to monitor the pods in Kubernetes and restart them if something hangs.
5. Special Features
- The pod requires the
NET_ADMINcapability to set Strongswan routing tables. - Production and staging differ not only in target systems but also in the number of connected external services.
- The entire tunnel runs in a dedicated service - other pods in the cluster do not need to know about it.
6. Pod Manifest
Here is an example of the K8s pod description:
apiVersion: v1
kind: Pod
metadata:
name: vpn-client
namespace: vpn
spec:
containers:
- name: vpn
image: your-vpn-image:1.0.0
imagePullPolicy: Always
envFrom:
- configMapRef:
name: vpn-client-configmap
ports:
- containerPort: 8080
name: ext-db-prod
protocol: TCP
livenessProbe:
exec:
command:
- /scripts/probe.sh
failureThreshold: 3
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 2
readinessProbe:
exec:
command:
- /scripts/probe.sh
failureThreshold: 1
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 2
startupProbe:
exec:
command:
- /scripts/probe.sh
failureThreshold: 40
periodSeconds: 5
successThreshold: 1
timeoutSeconds: 2
securityContext:
capabilities:
add:
- NET_ADMIN
7. Conclusion
The combination of Strongswan and Nginx is a robust, lightweight option to connect external services over VPN in Kubernetes. The strict separation by environments, flexible Helm templates, and Kubernetes probes make the solution production-ready - without overhead through additional tools.
8. Frequently Asked Questions
1. Why do I need a VPN in Kubernetes?
A VPN enables secure connections between your cluster and external systems, such as databases or legacy systems, that are not publicly accessible. It is particularly sensible when sensitive data needs to be transferred or direct IP communication is required.
2. What is Strongswan and why is it suitable for Kubernetes?
Strongswan is an established open-source VPN solution for IPsec-based tunnels. It is lightweight, reliable, and due to its modularity can be well integrated into containerized environments like Kubernetes.
3. How do I integrate Strongswan into Kubernetes?
Strongswan can be operated as a dedicated deployment in a pod. Through an adapted network configuration and iptables routing, the traffic is guided through the VPN. NGINX or other proxies handle the routing to the target system over the VPN.
4. Are there Helm Charts for Strongswan in Kubernetes?
No, there are no official Helm Charts. Most setups use custom deployments with Docker images, configuration files, and init scripts. This can be complex but enables maximum flexibility in VPN setup.
5. What are the alternatives to Strongswan?
Depending on requirements, you can also use WireGuard (modern, fast), OpenVPN (proven, but complex) or VPN services from cloud providers like AWS Site-to-Site VPN or Azure VPN Gateway.
























